THE BLOG
In this week's video, we look at creating a basic bash script in Kali Linux, a topic from a recently completed Ethical Hacking for Beginners course.
Enjoy the training!
In our latest YouTube video, we cover the LISP (Locator/ID Separation Protocol) feature, which is a topic on the CCNP Enterprise ENCOR (350-401) Exam Blueprint.
In this video, you’ll learn ho...
A fairly in-depth knowledge of BGP is required for ENARSI, so this video takes a look at how we can summarize (or aggregate) our advertised BGP networks. Summarization allow us to cut down the si...
In this video, you’ll get a tour of Kevin’s home network. The goal is to spark some ideas in you for your home network (or small business network). Kevin discusses 4 key design decisions, as well...
In keeping up with this month’s theme, CCNP Enterprise, this week’s training video looks at IP SLA, a topic found in the ENCOR (350-401) exam blueprint. IP SLA is an active method of monitoring a...
If you’ve been considering a focus in CCNP Collaboration, our latest YouTube video is a nice sample from our CLCOR (350-801) Video Training Series.
In this video, we consider how security works ...
In this video, we look at a topic found at the CCNP level, primarily in the ENARSI (300-410) exam: EIGRP named mode. If we’re going to be able to effectively troubleshoot EIGRP, we need to understan...
In this week’s video, you’ll learn about RIP, the Routing Information Protocol, a topic on CompTIA’s Network+ (N10-007) exam. Specifically, you’ll see three different versions of RIP and understa...
Just like any important device on the network, we need to backup our switches and routers periodically as well. If we have a catastrophic failure with a device, we don’t want to cost ourselves hours...
This week's training video is a replay from yesterday's live STP Deep Dive webinar. In this training, we cover every Spanning Tree Protocol (STP) topic on the CCNA (200-301) and CCNP ENCOR (350-401)...
This week’s training video takes a look at a section on the ENARSI (300-410) exam blueprint about troubleshooting BGP relationships.
Specifically, we cover the BGP multihop feature.
Happy...
Cisco’s Embedded Event Manager (EEM), a topic on the CCNP Enterprise ENCOR (350-401) exam, is a feature that can watch a router for a specific event and, if that event occurs, can trigger an action ...
You may have heard that Cisco has recently provided a new resource for CCIE studies: The CCIE Enterprise Infrastructure, Host VM. This custom Linux distribution allows us to experience the actual de...
This year’s Cisco Live was virtual, given the current circumstances our world is in with the pandemic. Even though we couldn’t all travel and meet in person, Charles and I still enjoyed participating ...
In this video, you’ll learn about Media Access Control (MAC) addresses. You’ll see the pieces and parts that make up the structure of a MAC address, in addition to a couple of examples of MAC addres...
In my latest training video, I cover the theory of Open Shortest Path First (OSPF) routing protocol.
OSPF is the most popular interior gateway protocol used today. In this video, you’ll under...
Whenever someone asks me what direction they should focus their IT career, particularly in regard to cybersecurity, my answer is always the same: “It depends.” It’s usually not a very satisfying answe...
In this week's training video, Charles takes a look at the configuration of VRF-lite. VRF stands for virtual routing and forwarding, or sometimes we see that called VPN routing and forwarding. Th...
We’ve all heard the saying, “Hindsight is 20/20.” However, a lack of clairvoyance about the future shouldn’t prevent us from boldly taking our next career step.
Steve Jobs told us, “You can't connect...
In this week's training video, Charles takes a look at how we interact with Cisco Meraki by way of the API, a topic straight out of the DevNet exam track. Charles also shares free resources in th...
This video is a sample from our CCNA (200-301) Video Training Series, and it gives us a high-level overview of three configuration management utilities: Puppet, Chef, and Ansible. These are new n...
This week's training video is a sample from our recently released SCOR (350-701) Video Training Series, which you can find over on our website.
Specifically, this week's video considers IOCs, wh...
This video is a sample from our upcoming CLCOR (350-801) Video Training Series, which is being released February 2021.
In this training video, we'll consider SIP, which is short for Session Initiat...
Charles has been wrapping up production on the SCOR (350-701) Video Training Series this week, so we thought it’d be fitting to go over one of the topics on the blueprint with you!
In this video...
In this week's video, we cover Time-Based Access Control Lists (Time-Based ACLs). With Time-Based ACLs, you can restrict access between specific devices based on time-of-day or day of the week. Enjo...
In this week's video, Charles looks at data loss prevention (DLP) policies within the Cisco Email Security Appliance (ESA), a security solution outlined in the SCOR (350-701) exam blueprint.
Enjoy ...
As we approach Thanksgiving Day here in the states, I've been reflecting on what I'm thankful for this year. Even though 2020 has been a very unique year, I'm thankful for lots of good things that hav...
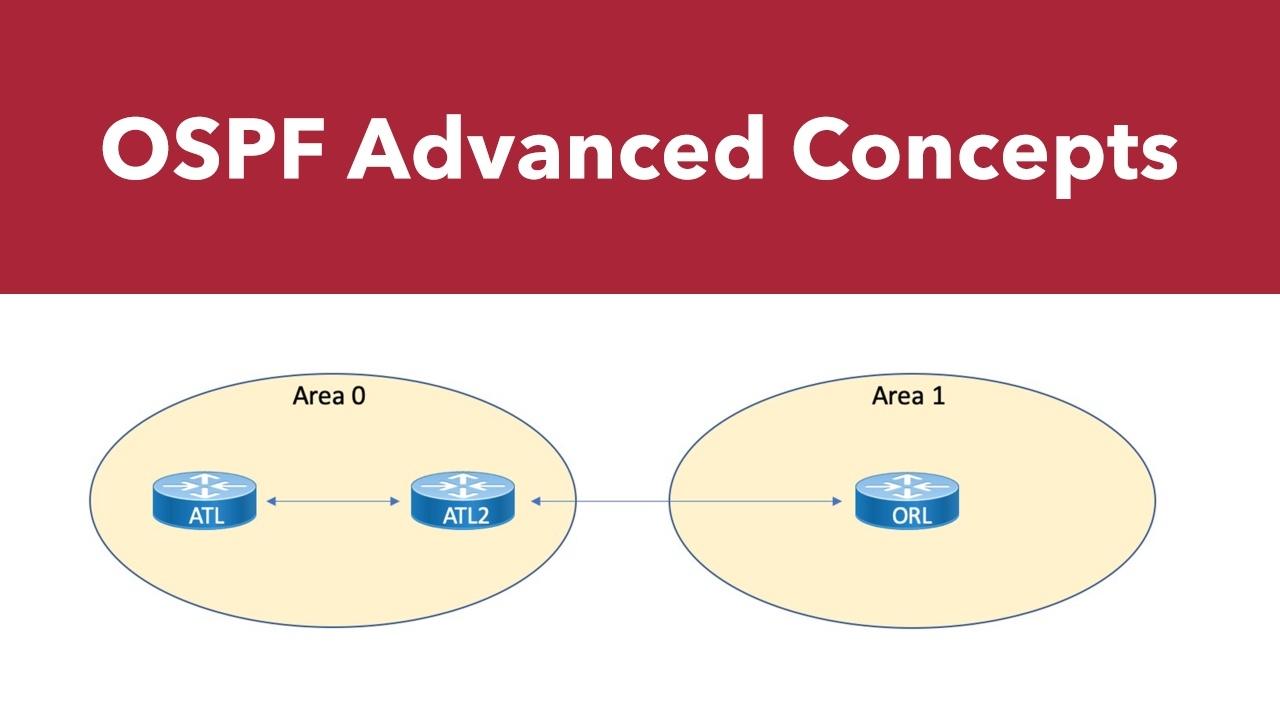
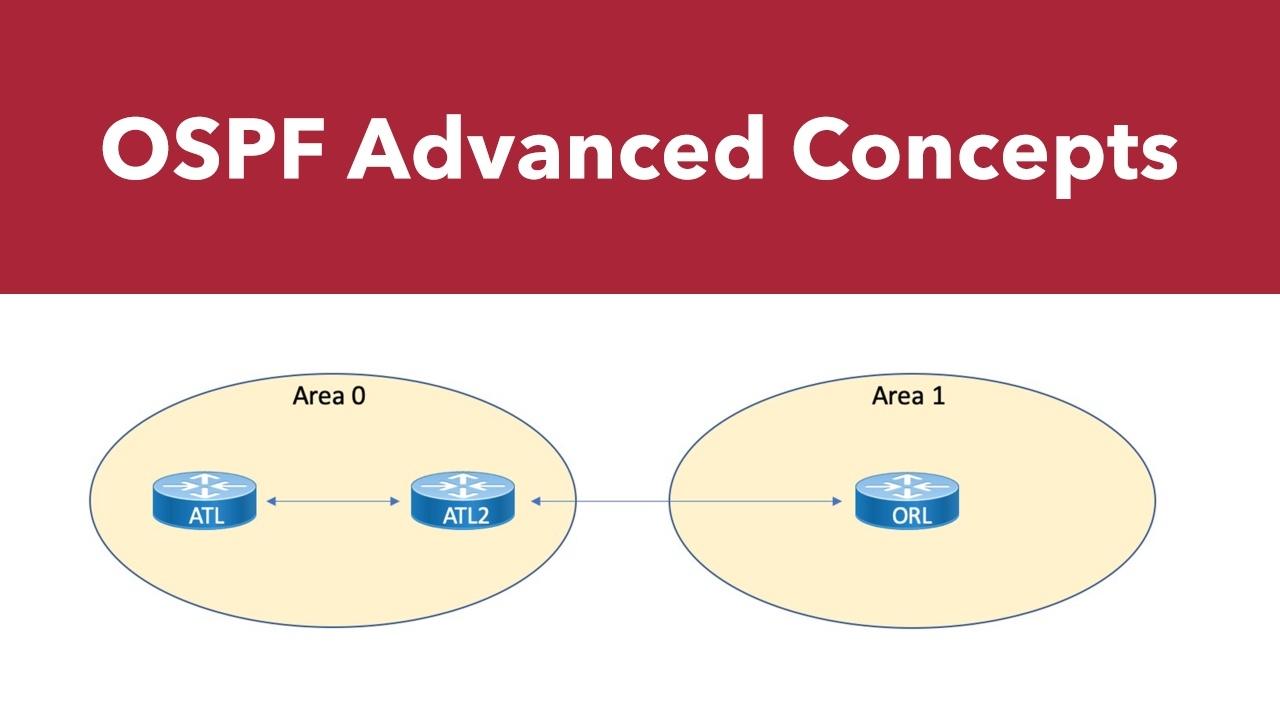
In the previous part of our OSPF series, we examined options for manually filtering routes. As we wrap up our look at advanced OSPF topics, we'll discuss default routes, and compare OSPFv2 with OSPFv3...
In our previous blog post, we examined how OSPF can automatically filter routes through the use of special areas and LSA Types. But what about your options for manually filtering routes in OSPF? In th...
Last time, we began our look at advanced OSPF topics with the configuration of backbone and non-backbone areas. In this blog post, we'll look at the creation of more specific area types.
Stubby Area
...The time has arrived to tackle some of the more advanced (and interesting) features of the Open Shortest Path First routing protocol. We begin by examining the configuration and verification of the di...
Before we move on to more advanced topics, we'll wrap up this OSPF Basics series in Part 3. Here we'll examine LSA types, area types, and virtual links.
OSPF LSA Types
Link State Advertisements (LSA...
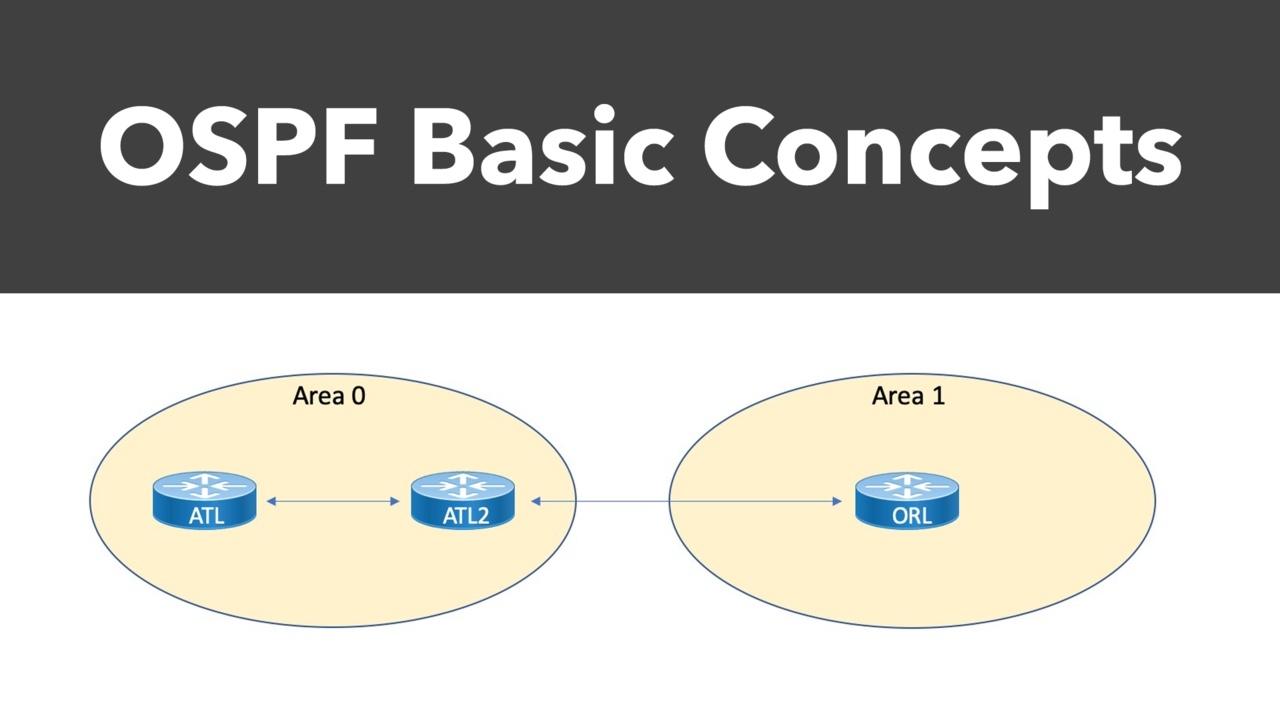
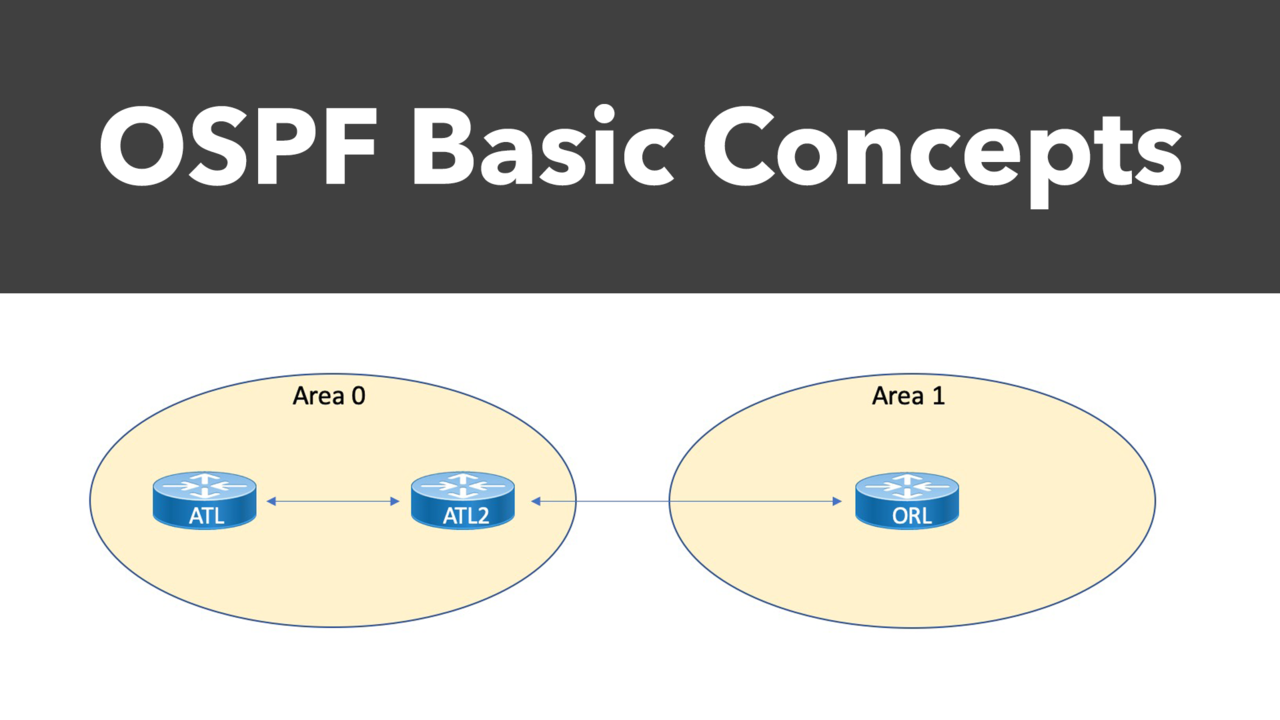
In the previous blog post, we looked at a few fundamental OSPF concepts, including neighbor and adjacency formation. As we continue through the basics of OSPF, this post will examine router roles, tim...
The OpenShortest Path First (OSPF) dynamic routing protocol is one of the most beloved inventions in all of networking, widely adopted as the Interior Gateway Protocol (IGP) of choice for many network...
One of the big announcements this week at Cisco Live was the launch of their new DevNet certification track. Cisco CEO Chuck Robbins reiterated the fact that knowledgeable engineers are always going t...
By now I'm sure you've heard of the sweeping changes Cisco is making to their certification tracks, which was announced at Cisco Live on Monday June 10, 2019. I covered the CCNA exam changes in a prev...
On Monday June 10, 2019 Cisco announced an unprecedented revamp of their certification program. This post dives into one of the major updates, the new CCNA certification. (We'll have a future blog pos...
Cisco just announced their certification program is getting a MAJOR update. Here’s what you need to know:
CCNA Updates
- A new CCNA exam will be released on February 24, 2020.
- This new CCNA certifi ...
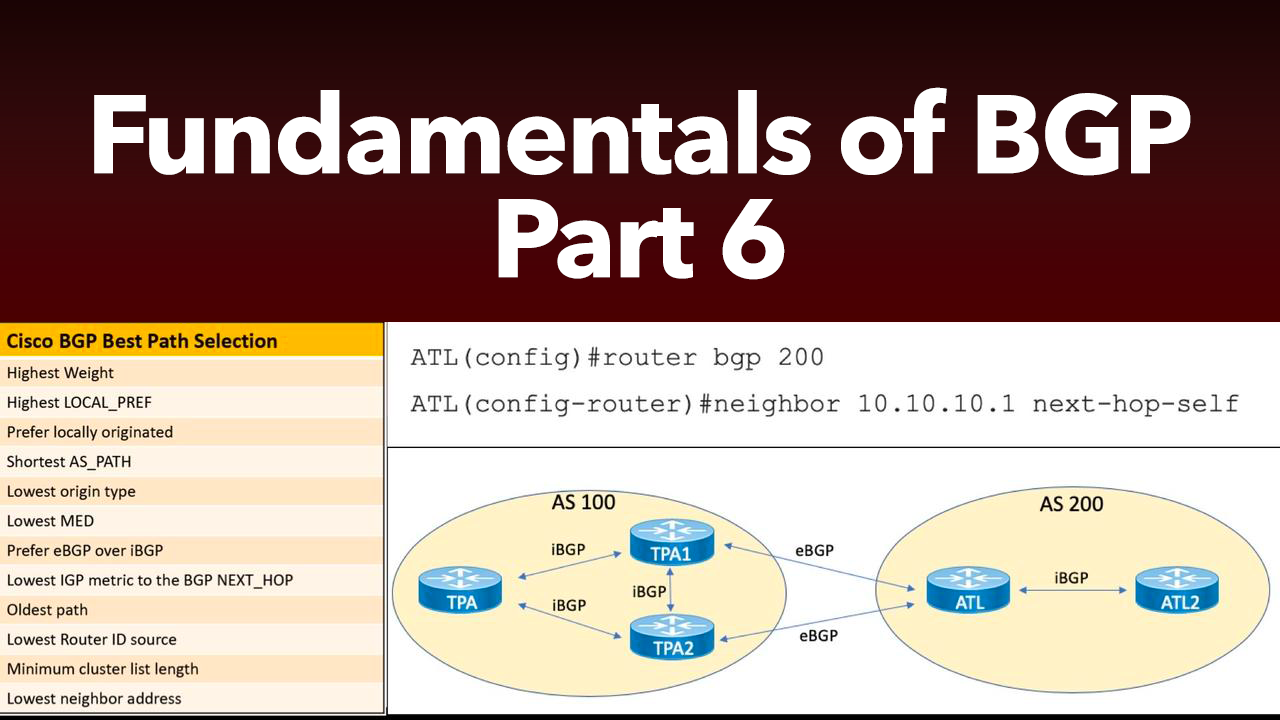
This post is the 6th and final in a series of Border Gateway Protocol (BGP) posts. If you missed any of the first five parts, here are the links:
This post is the 5th in a series of Border Gateway Protocol (BGP) posts. If you missed any of the first four, here are the links:
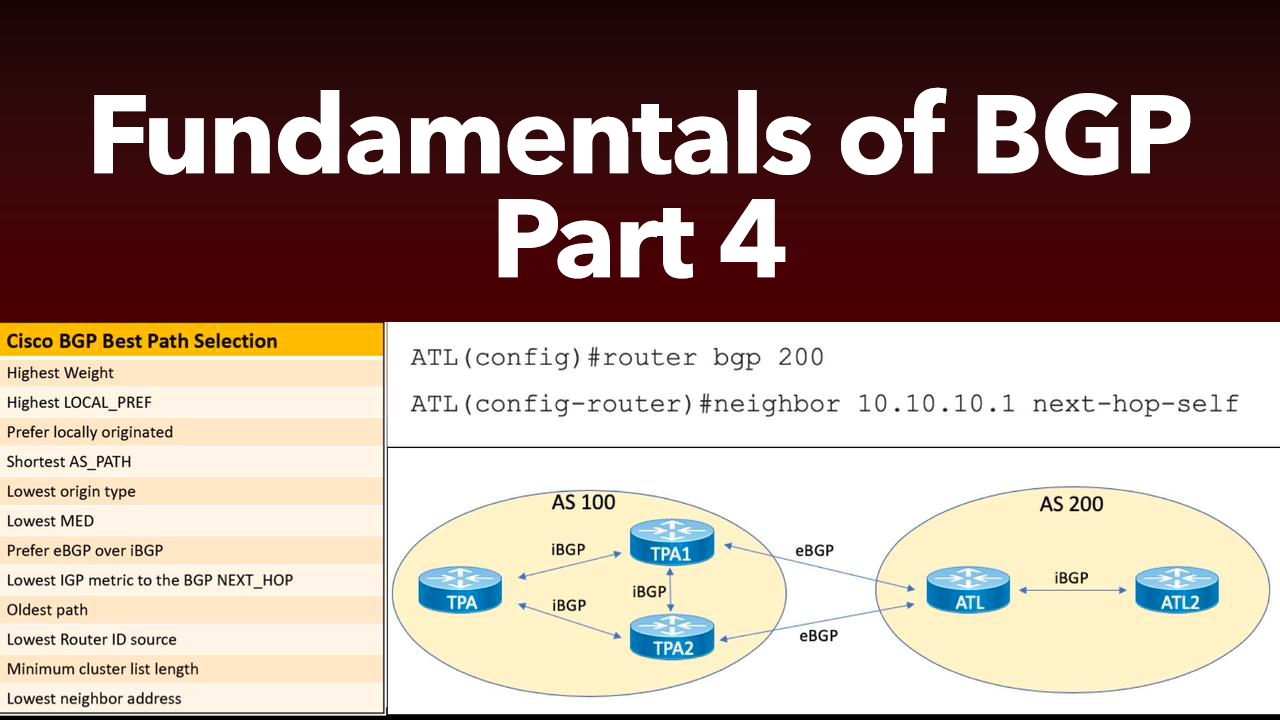
This post is the 4th in a series of Border Gateway Protocol (BGP) posts. If you missed any of the first three, here are the links:
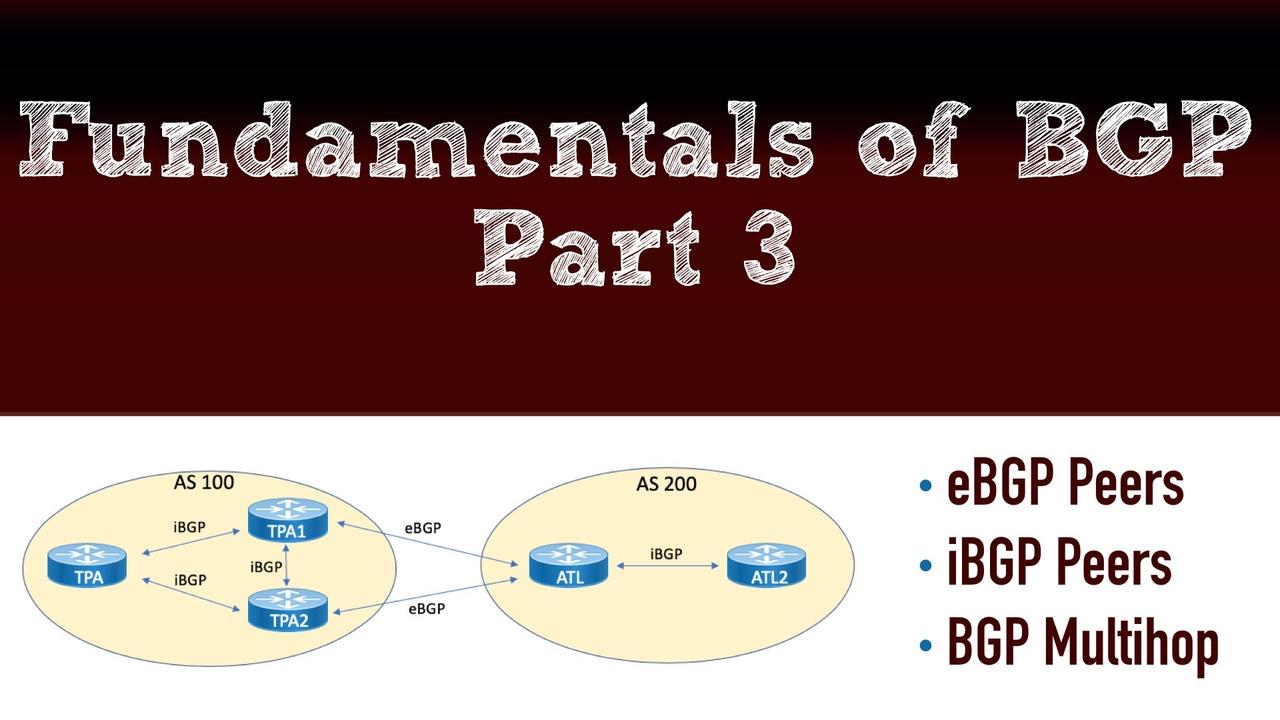
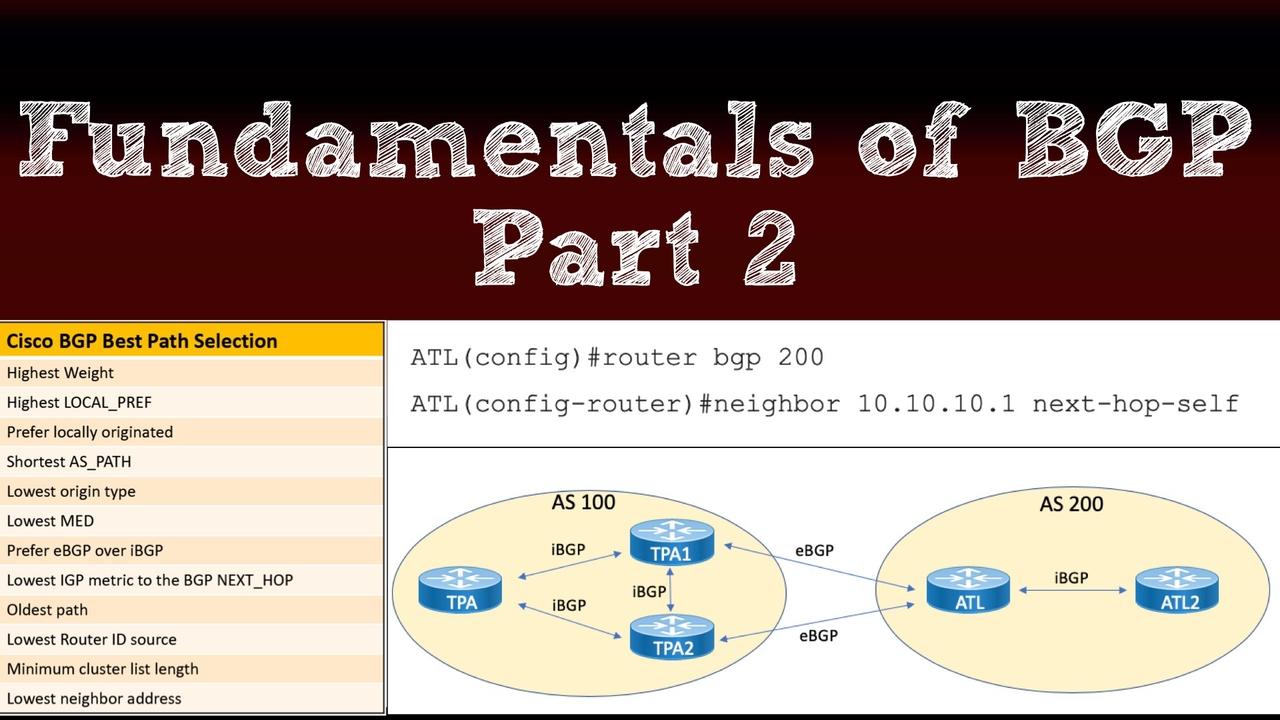
This post is the 3rd in a series of Border Gateway Protocol (BGP) posts. If you missed either of the first two, here are the links:
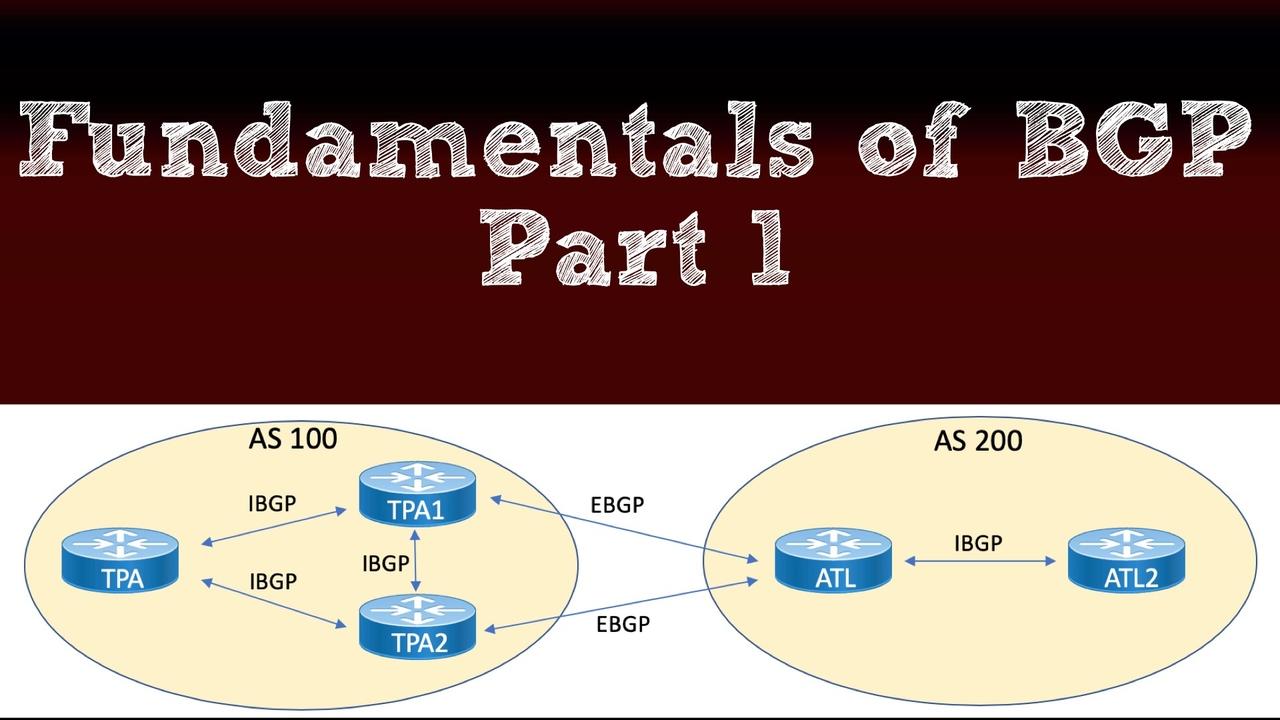
Part 1 of our blog series on Border Gateway Protocol (BGP) gave you an overview of BGP and then delved into BGP message types and neighbor states. Now, in this post, you'll learn about one of the mos...
One of the most intimidating topics for Cisco certification candidates in the Route/Switch track is Border Gateway Protocol (BGP). To help remove the FUD (Fear, Uncertainty, and Doubt) surrounding BGP...
As a redundancy measure, it’s possible to deploy multiple Cisco ASAs together in a failover configuration, also known as a High Availability Implementation. This requires that the ASAs have identical ...
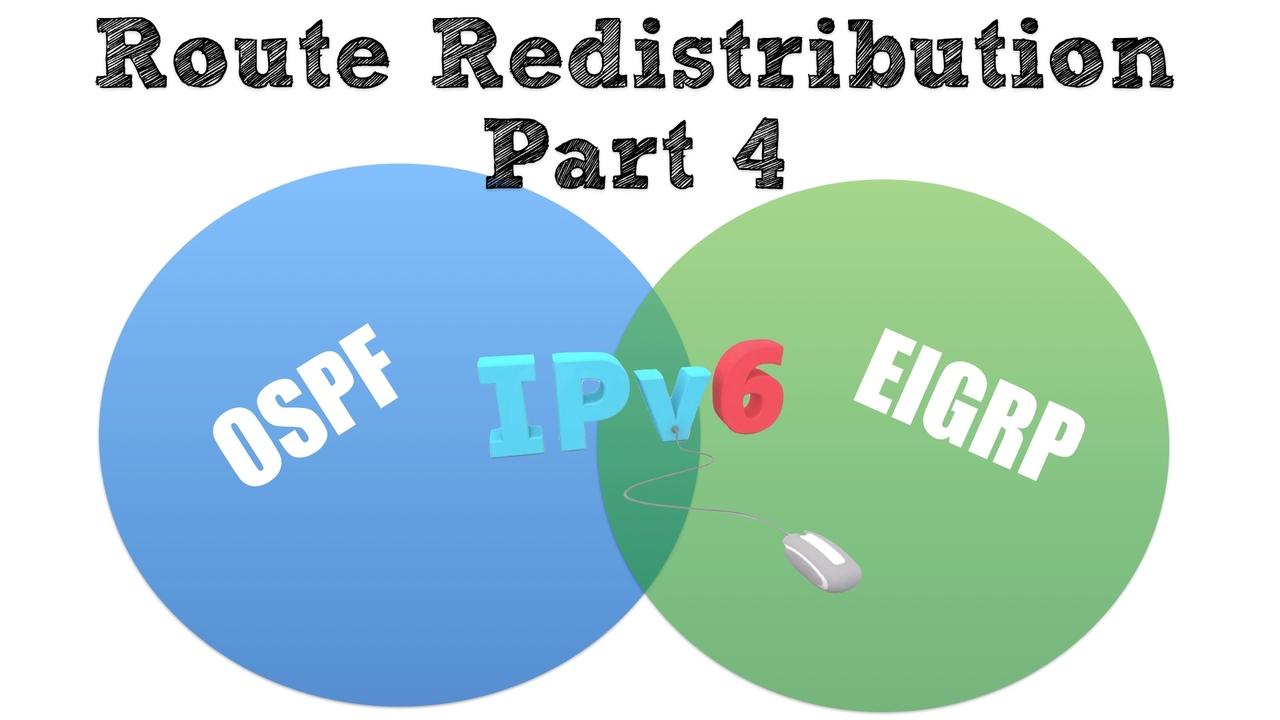
This post is the fourth in a series of posts on route redistribution. If you haven't yet read the first three, here are the links:
Cisco Zone-Based Policy Firewalls are a more modern implementation of the interface-based stateful inspection. This allows you to group interfaces into zones, which have similar functions or features....
In this video, you'll learn how to download (for FREE) Cisco Packet Tracer.
Then, you'll load a .PKT file (click HERE to download your .PKT topology file) into your copy of Cisco Packet Tracer and co...
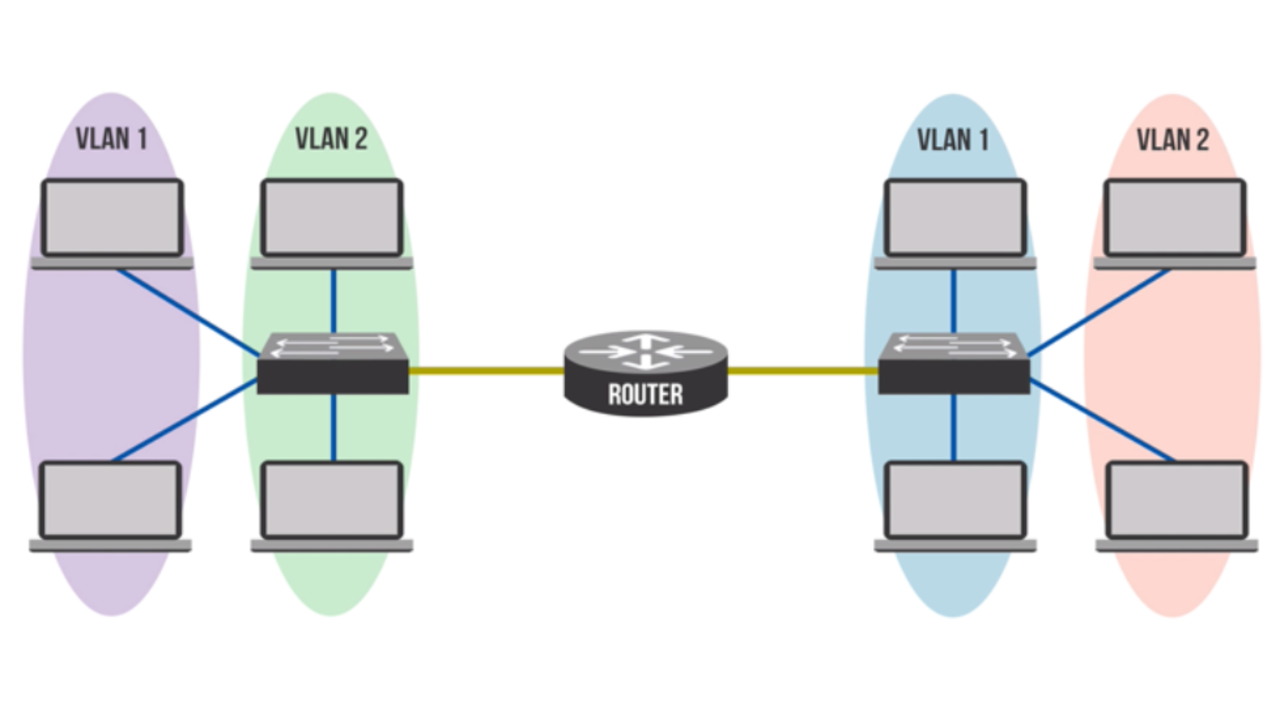
A Virtual Local Area Network (VLAN) is a logical grouping of devices on one or more LANS, configured to communicate as if they were on the same segment. In order to communicate with devices in another...