THE BLOG
It's another one of those buzzwords we're hearing a ton these days, the Internet of Things, or IoT for short.
But what exactly is it, and how's it going to impact us as networking professionals? That...
Sometimes, we might want a router interface to participate in an EIGRP routing process (in order to advertise that interface's network) without that interface sending out EIGRP Hello messages. That's ...
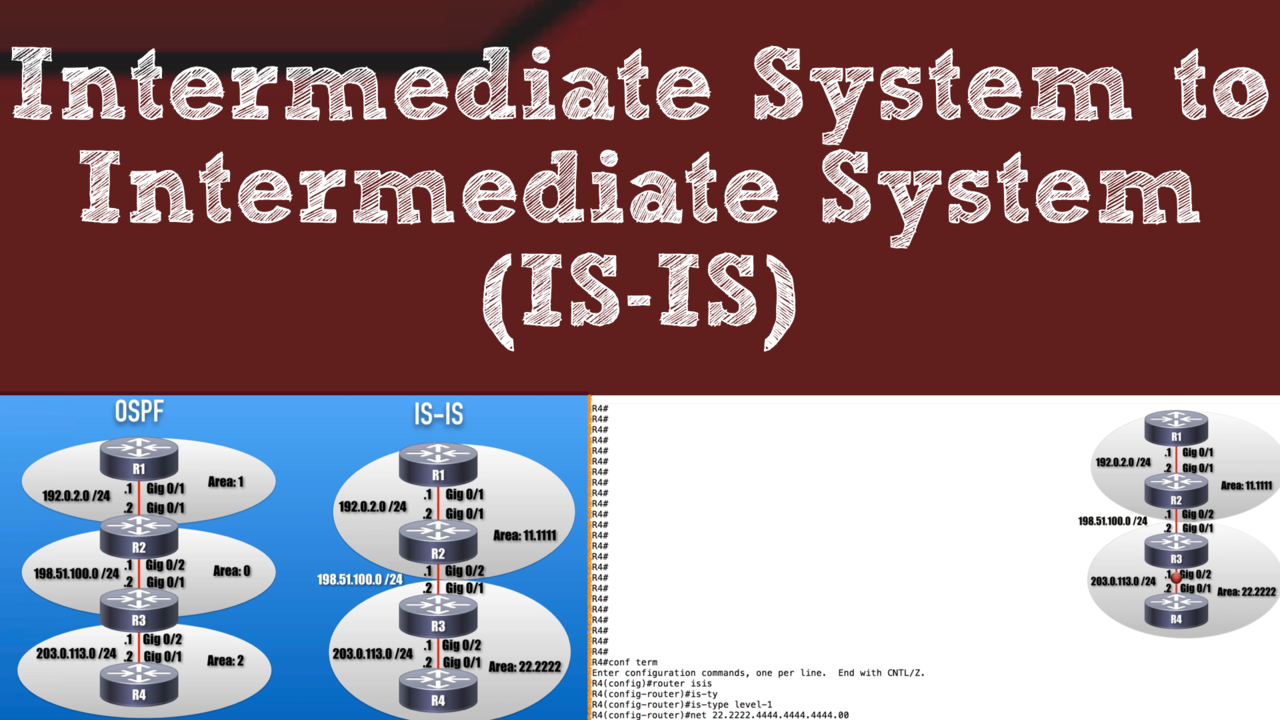
In our Cisco routing and switching studies, we commonly study routing protocols such as RIP, OSPF, EIGRP, and BGP. However, there's a very scalable, fast converging, link-state routing protocol that o...
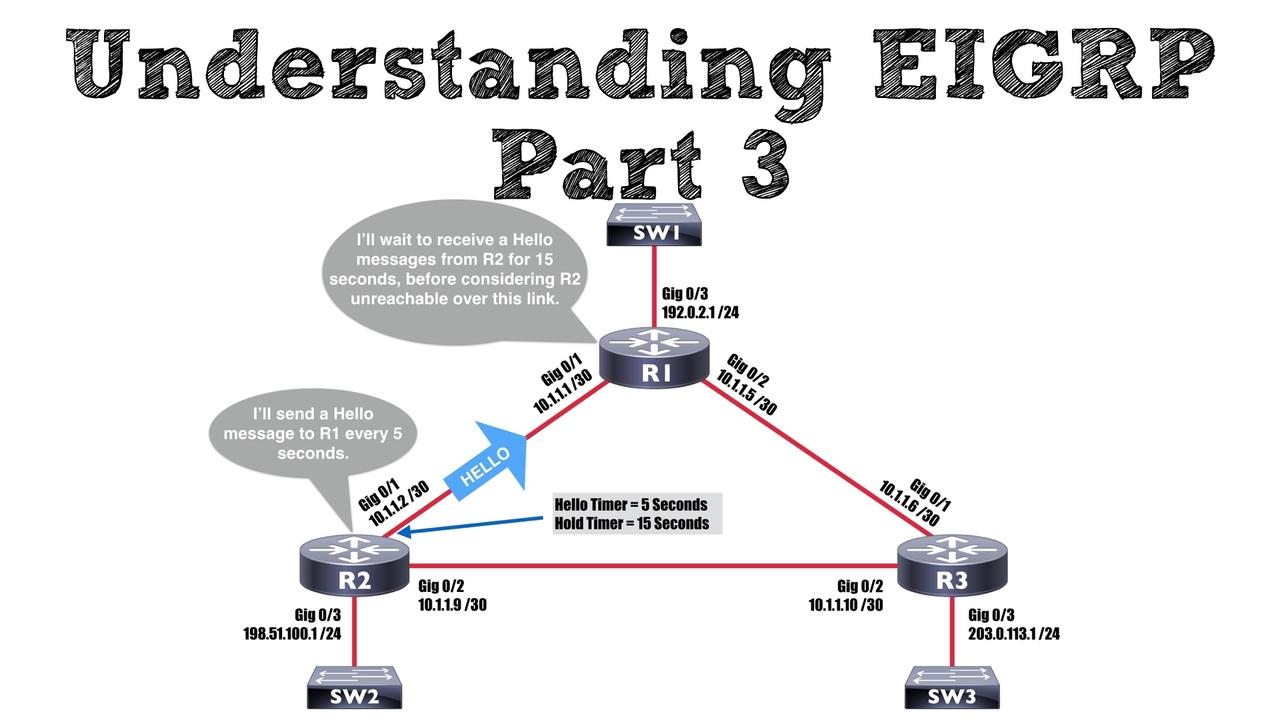
Once of EIGRP’s claims to fame is its fast convergence in the event of a link failure. However, one thing that might slow down this convergence is timer configuration. That's the focus of this blog po...
One of the buzzwords you hear a lot in our industry these days is Cisco IWAN. But, what exactly is Cisco IWAN, and what can it do for us? That's what you'll learn in this video.
One of the big buzzwords you hear surrounding tech startups is pivot, which is what happens when a company is moving in one direction and makes a strategic decision to go in another direction. For exa...

In the first blog post in our Understanding EIGRP series, we were introduced to EIGRP’s features, in addition to a basic configuration example, and a collection of verification commands. Now, in thi...

I used to work as a Network Design Specialist at Walt Disney World, in Florida. Their massive network contained over 500 Cisco routers (and thousands of Cisco Catalyst switches). What was the routin...
If you’re studying for a Cisco certification, you might be debating what to do for your hands-on practice. Will you buy a home lab? What about using a simulator or an emulator?
Well, before spendin...
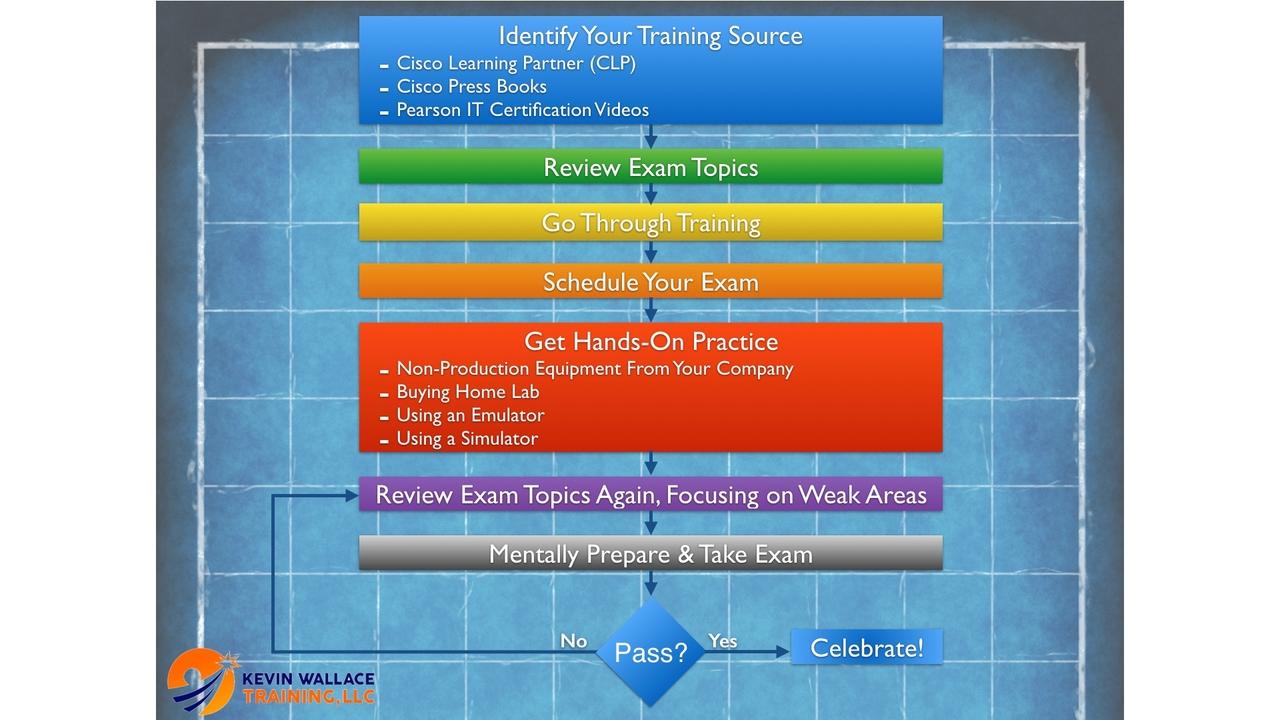
You want to get your first (or next) Cisco certification, but do you have a specific preparation strategy, or are you just winging it? If you do have a structured framework you’re confidently executin...
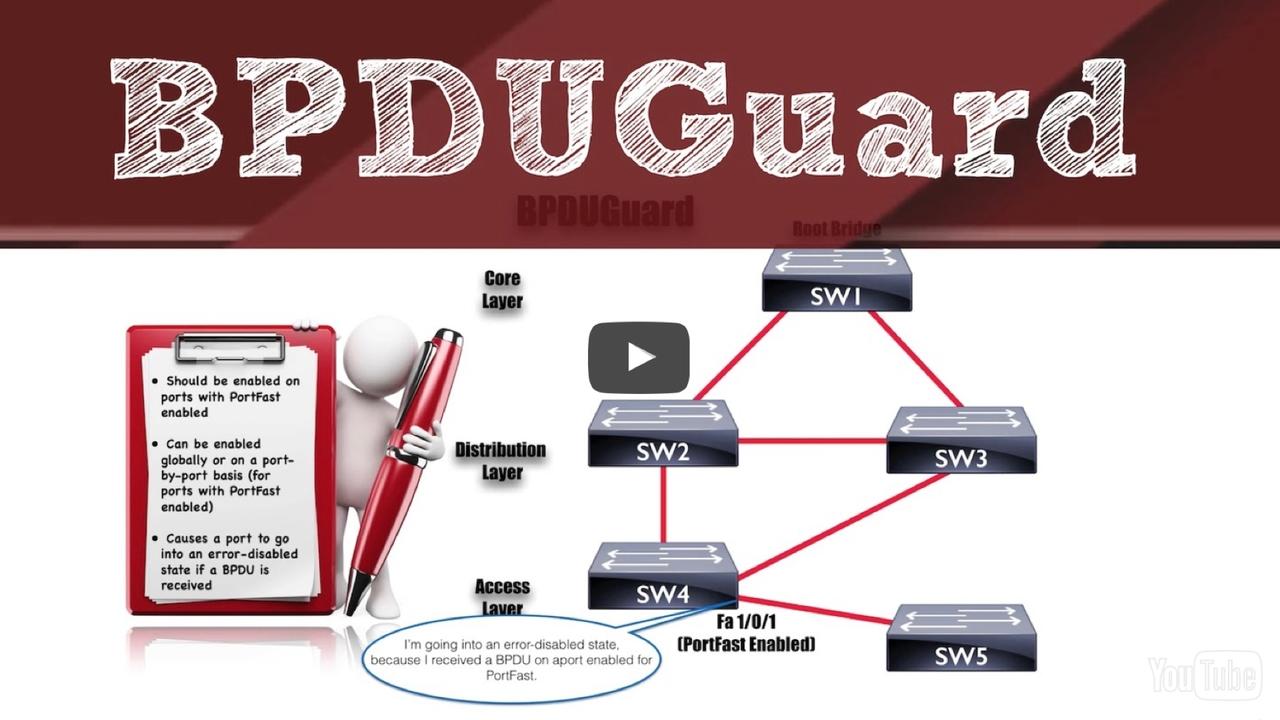
Yet another new topic on the new CCNA R/S v3 exam is BPDUGuard, which is an enhancement to Spanning Tree Protocol (STP) available on our Cisco Catalyst switches. Specifically, BPDUGuard can help preve...
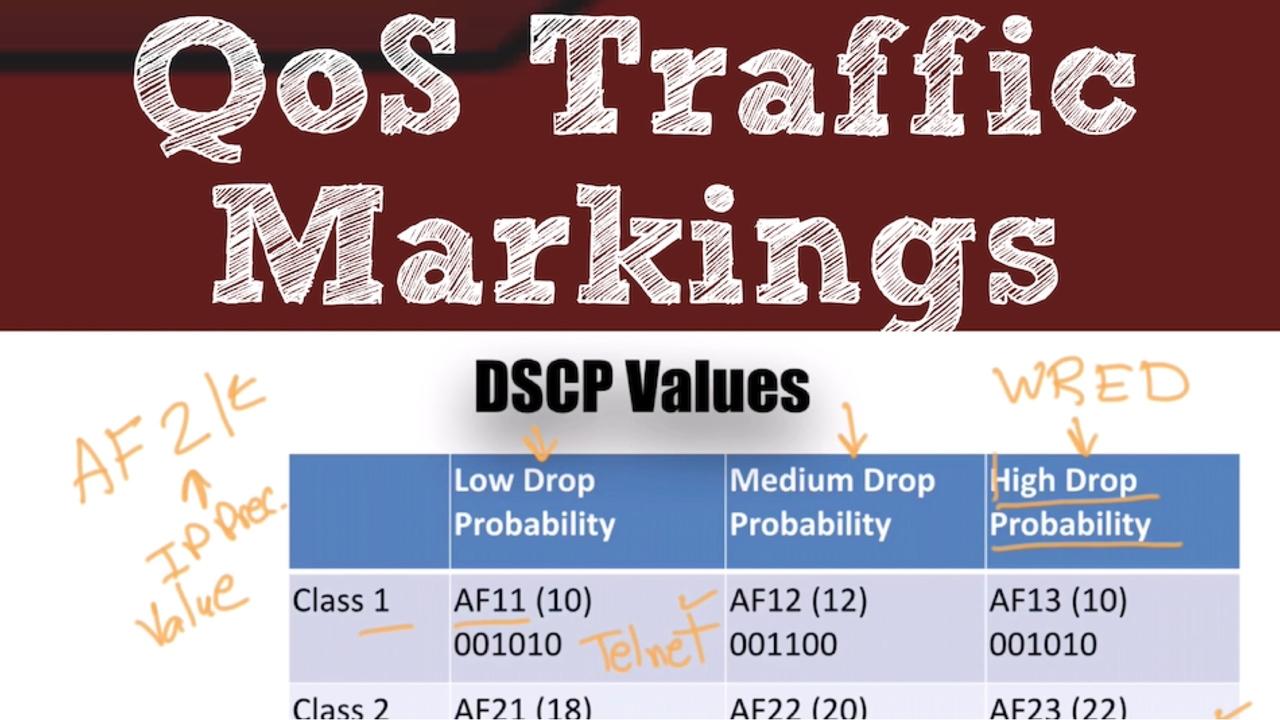
One of the new topics on the new CCNA R/S v3 exam is Quality of Service (QoS). Having taught QoS for many years, I’ve noticed that one of the topics students find most challenging is QoS Traffic Marki...

You’ve earned your certifications. Maybe you have a college degree, and hopefully some technical experience. Now, it’s time to sell yourself to a prospective employer. We all know first impressions ...
When you’re reviewing the list of topics on the new CCNA R/S version 3 exam, one topic that’s sure to stand out is the APIC-EM Path Trace ACL Analysis Tool. That’s a very long name for a very new feat...

The recently announced CCNA R/S version 3 includes a collection of topics falling under the category of Network Programmability. The underlying technology here is Software Defined Network (SDN), whi...
A Wide Area Network (WAN) is a network with geographically separate locations, and these locations can be interconnected in a variety of topologies. This video shows you the three WAN topologies you n...
The new CCNA R/S version 3 exam requires you to know how to configure static routing, for both IPv4 and IPv6 networks.
This video, which is a sample from my upcoming CCNA R/S v3 Complete Video Cour...

There are lots of things that I intend to get around to, sooner or later. One day, I’m going to clean out a bunch of old clothes from my closet. One day, I’m going to clean out my garage, and get it...
For me, the addition of QoS to the list of topic areas for the new CCNA R&S version 3 exam was a great thing. The reason is, QoS is my absolute favorite Cisco topic. So, I couldn’t wait to start recor...

It’s a timeless paradox… “How can I get a job without experience, and how can I get experience without a job?” If you find yourself in such a situation, this blog post is going to show you a couple ...
You’re probably familiar with the concept of virtualization, where you can run multiple virtual servers on a single physical server. However, did you know that you can run multiple virtual routers ins...
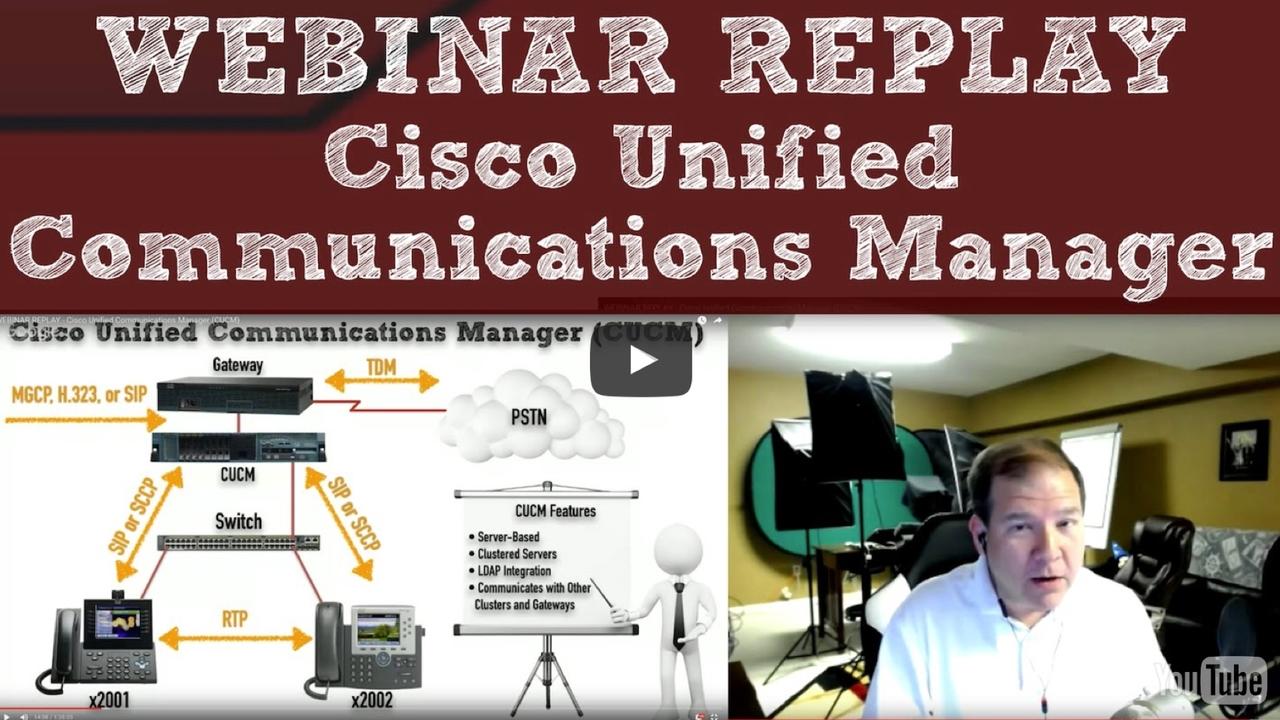
Earlier this month, I did a live webinar covering the theory and configuration of a CUCM server. If you missed it, you can check out a replay below.
Also, at the end of the webinar, I offered a big d...

It happens about every three years or so; Cisco updates its flagship certification, the CCNA in Routing and Switching. Today (May 17, 2016) is such a day, and current and future certification candid...
Are you preparing for your CCNA, CCNP, or CCIE in Collaboration? If so, check out this video that gives you a step-by-step demonstration of a Cisco Unity Express (CUE) module configuration. And here’s...
When I was around 20 years old, I used to go into bookstores and look for a book (something on a technical topic, a business biography, or on personal development) that I could afford. However, I rece...
In this video we’re covering the fundamental concepts surrounding the IP, ICMP, UDP, and TCP networking protocols. Having a solid understanding of these protocols is critical to just about everything ...
You might have seen some of my recent Cisco Collaboration videos. Interestingly, the big difference between Cisco’s new Collaboration track than its prior Voice track is the addition of video technolo...
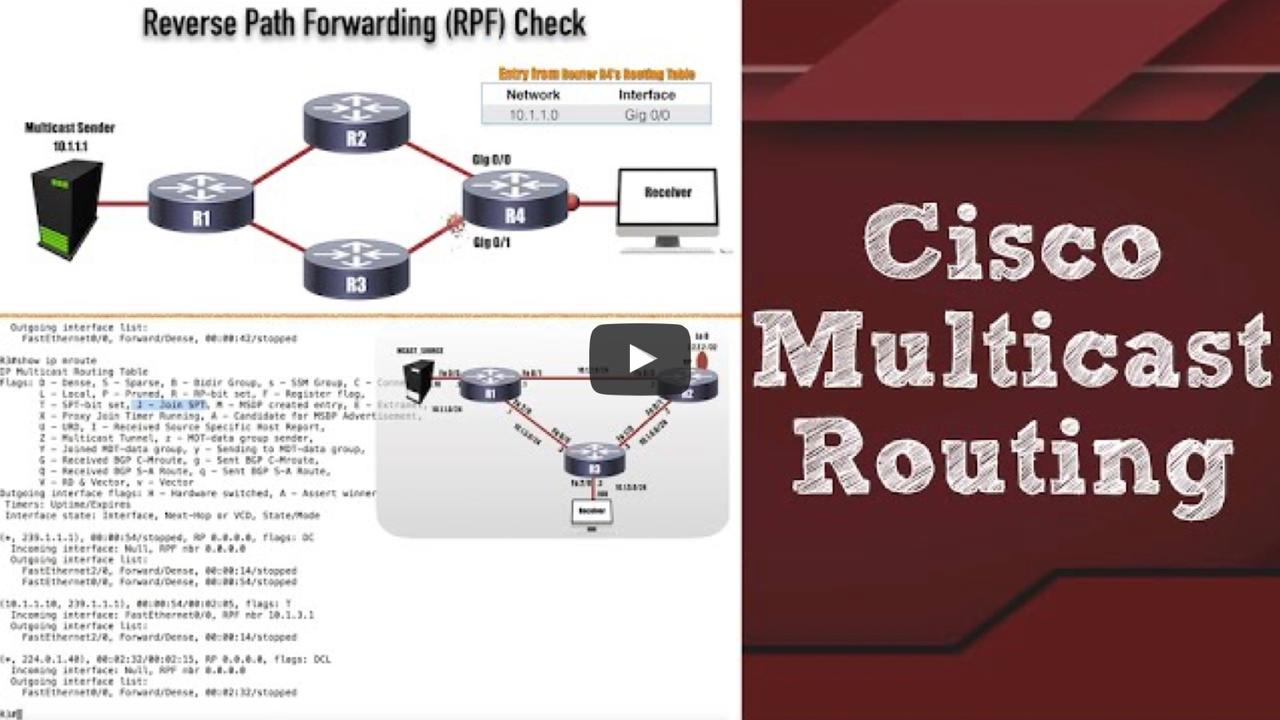
In this new video, you’ll get a simplified, yet comprehensive, look at multicast routing on Cisco routers. This video is appropriate if you work with multicasting in the real world or if you’re studyi...
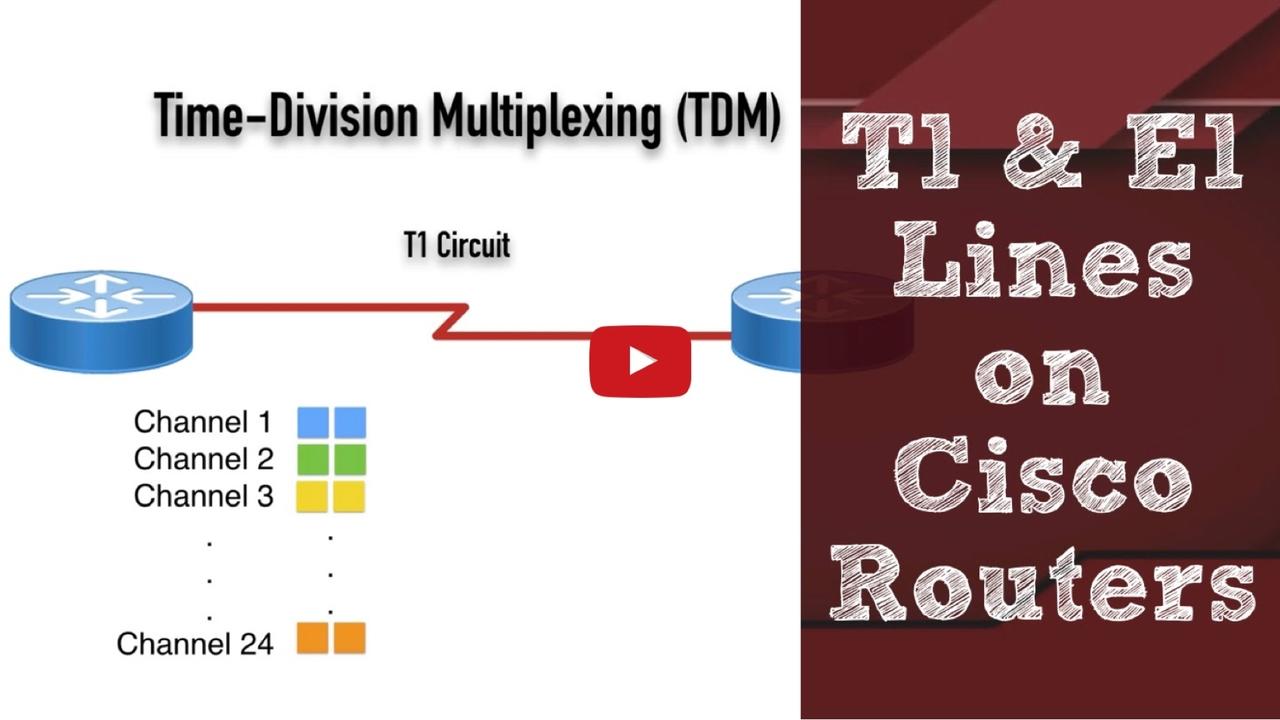
In this new video, you’ll learn the theory behind T1 and E1 circuits and how to configure them on your Cisco routers. This is a key technology to master for Cisco CCNA Collaboration, CCNP Collaboratio...
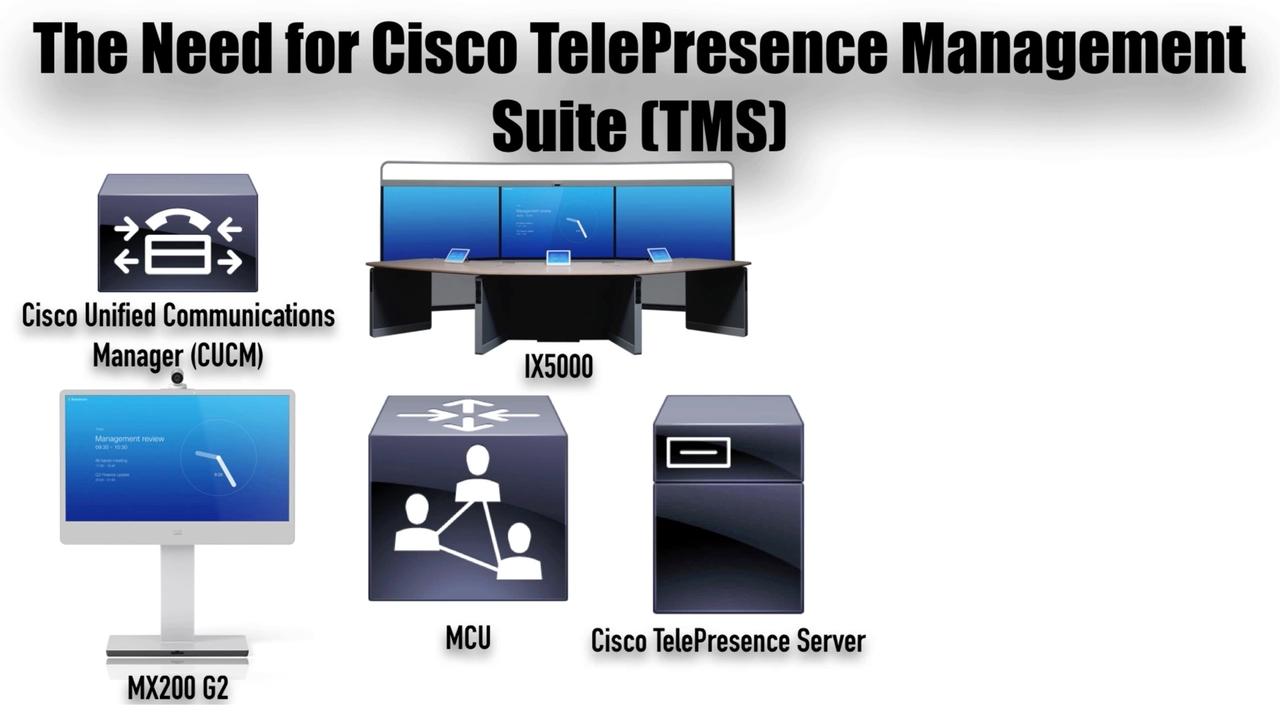
For the past few months, I’ve been immersed in Cisco collaboration technologies, and I created a video for you to introduce you to the 6 core systems that make up a Cisco collaboration network.
Th...

Having the appropriate Cisco initials after your name (e.g. CCNA, CCNP, or CCIE) is a shortcut way of letting someone know your relative skill level. Even if you’ve got the skills and are at the top...

Have you ever used some sort of virtualization software (e.g. vmware) to get multiple virtualized servers running on a single physical server? It’s a great way to save resources, by eliminating the ...

While documentation is indispensable in your mastery of Cisco technologies, at some point you have to “get your hands dirty.” In other words, you have to actually configure the routers, switches, an...
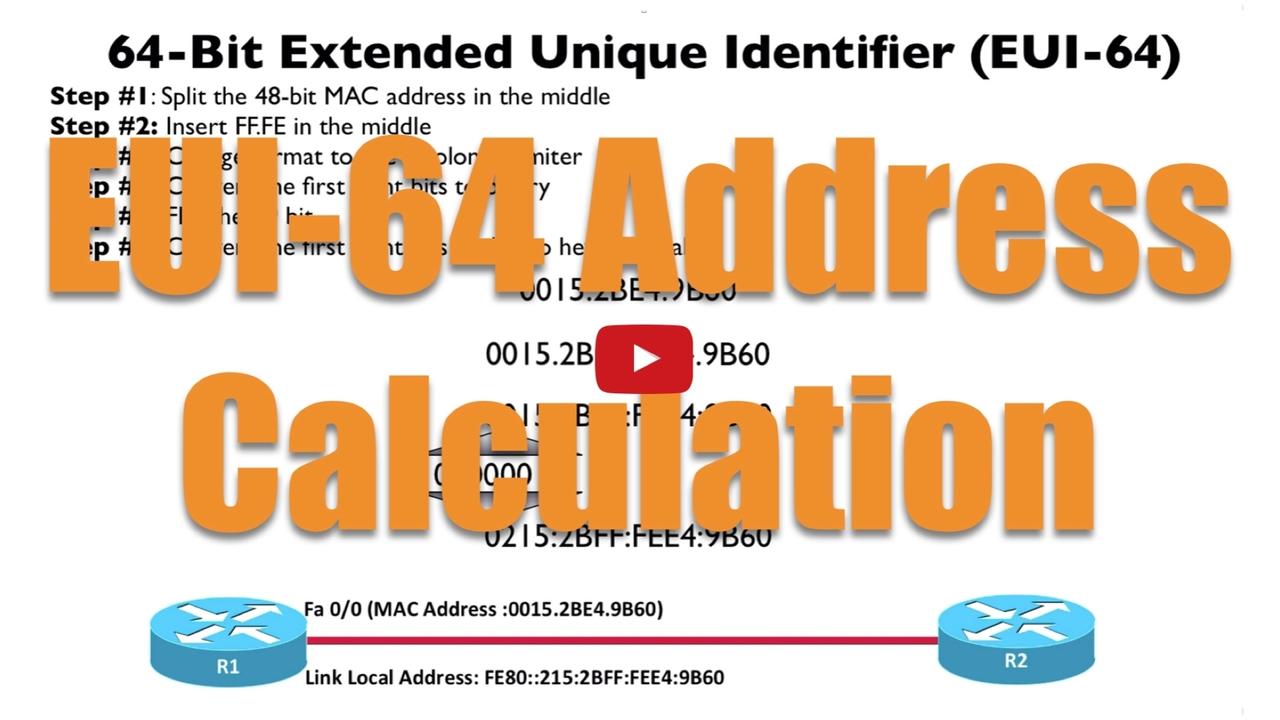
An IPv6 address is 128 bits in length, and like an IPv4 address, it’s divided into prefix bits (representing the network segment) and host bits (uniquely identifying a host on that network segment). A...

In high school, I really, really disliked reading. My reading speed was slow, and I found most of the assigned books were boring to me. Since this was back in the 1980s, before audio books really to...

If you’re preparing for the CCIE R&S Written Exam or Lab, you need a collection of training materials. Perhaps you watch some training videos; you download a few whitepapers from Cisco’s website; an...
Amajor challenge for CCIE R/S Lab candidates is getting their hands on a huge topology, similar to what they’ll face in the actual lab. One option is to use the CCIE Lab Builder, and you can check out...
How do you get hands-on experience when you’re preparing for your CCNA R/S or CCNP R/S certifications? One option is using the Cisco Learning Labs. You can check out my review here.
Links to Purcha...

While having lofty goals is key to propelling your career into the stratosphere, if you don’t have time to take action on your goals, what good are they? I shouldn’t say that you don’t have time. Af...
The way you start your day can have a huge impact on your productivity. Over the past few months, I’ve been experimenting with creating a “morning ritual,” which is a collection of energizing and moti...
Walt Disney is one of my personal heroes, and the following quote from him beautifully sets the stage for this blog post’s topic, curiosity:
We keep moving forward, opening new doors, and doing new t...
Even if you know how to setup every technology on the CCIE Collaboration Lab, you can still fail if you don’t troubleshoot effectively. Not only will you need to troubleshoot any configuration mistake...
Are you preparing for the CCIE Collaboration Lab? If so, this new video can dramatically improve your odds of passing the lab.

Kevin Wallace, CCIEx2 (Collab. & R/S) #7945
If you enjoyed this ...

Cisco recently retired their CCNA Voice and CCNP Voice tracks, and have replaced those telephony-centric tracks with the new CCNA Collaboration and CCNP Collaboration tracks. While these tracks do c...
In a previous blog post we considered how to effectively set our goals to reach our “destination address.” However, no matter how well we plan, it seems that occasionally, life gets in the way. That’s...
This video shows you how the Enhanced Locations feature of CUCM operates, and is one of the many bonus videos included as part of the upcoming CCIE Collaboration Lab Walkthrough video series from Kevi...
When you see an advertisement for Disney Parks, and they show their tag line, The Place Where Dreams Come True, you might conjure up images of children meeting their favorite pirate or princess (by th...
About three years ago, I wrote a little e-book entitled Your Route to Cisco Career Success. Although it’s available in Kindle format from Amazon, you can download a free PDF of the bookHERE. Since the...
The thought of attaining a CCIE in Collaboration might seem like a daunting task. After passing the CCIE Voice Lab (the predecessor to the CCIE Collaboration Lab), I remember making the statement that...
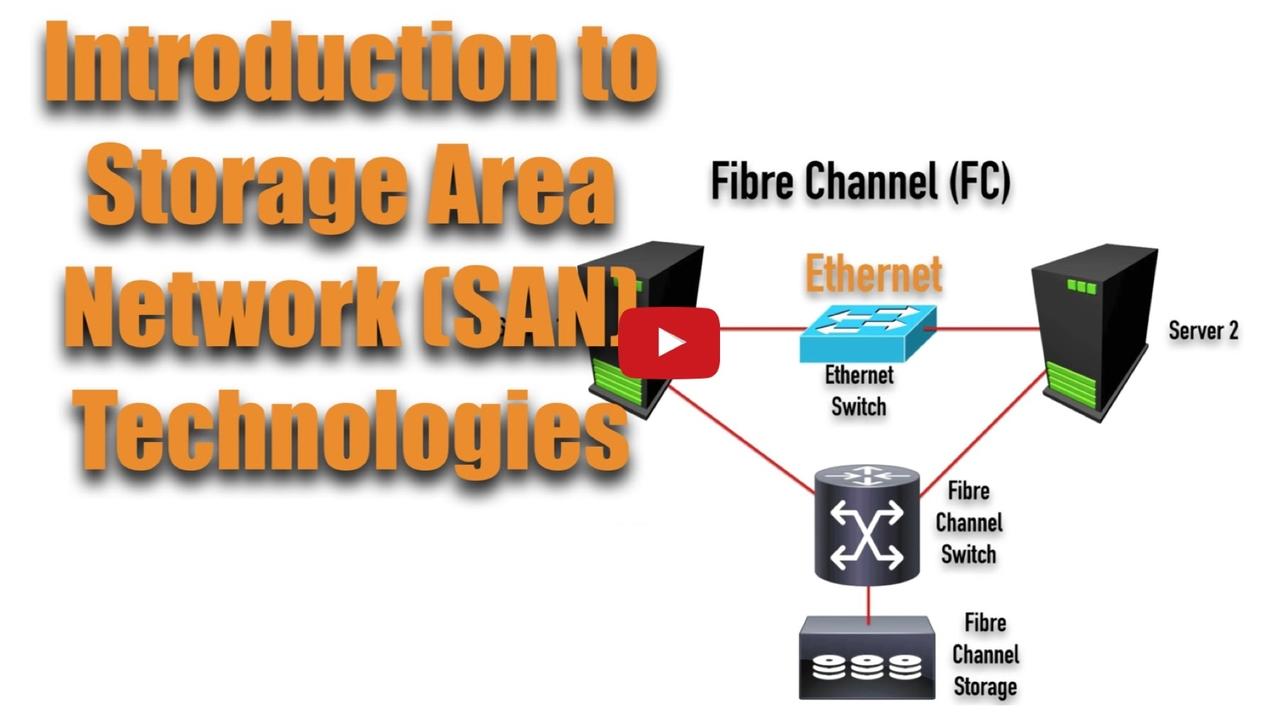
Storage Area Networks (SANs) allow devices (e.g. PCs or servers) to store and retrieve data from hard drives that are attached somewhere on a network, as opposed to being directly attached to the devi...